Authentication using the SAML standard
SAML (Security Assertion Markup Language) is a standard that allows the exchange of information for Single Sign-On (authentication and authorization) between different parties (applications). The participants in this authentication are the identity provider and the service provider.
The service provider is the entity that grants a user permission or access to a resource. Fracttal acts as the service provider.
The identity provider is the entity that has the necessary infrastructure for user authentication. In this case, the identity provider is the application that has registered the users and controls their access. Some examples of applications that can serve as identity providers are Active Directory, Okta, among others.
Through SAML, a service provider connects with an identity provider online to authenticate users attempting to access secure content.
One of the identity providers
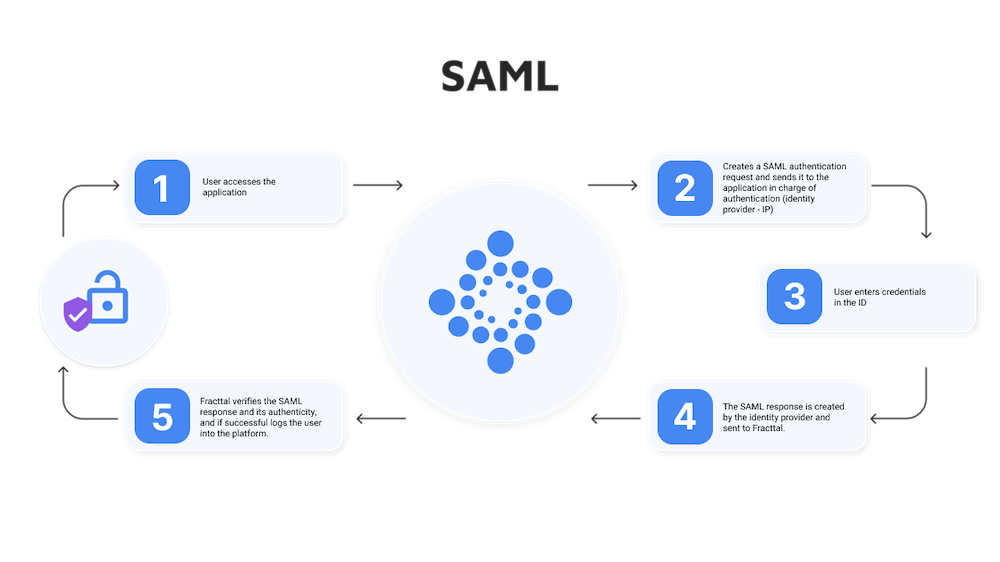
AUTHENTICATION USING SAML IN FRACTTAL
To use Single Sign-On authentication in Fracttal via the SAML standard, you must configure it in the Configuration Module at https://one.fracttal.com/config under the Security – SSO option:
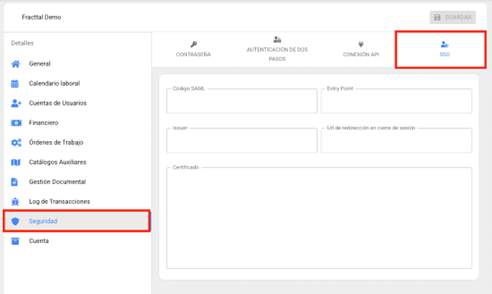
In this SSO configuration, you must enter the identity provider information:
| FIELD | DESCRIPTION |
|---|---|
| SAML Code | Communication Name |
| Entry Point | URL where Fracttal sends a SAML request to initiate the login. |
| Issuer | Also referred to as EntityID. Contains information that the identity provider uses for internal verifications. |
| Logout Redirect URL | URL where information is sent when the user logs out of Fracttal. |
| Certificate | Authentication certificate issued by the identity provider. |
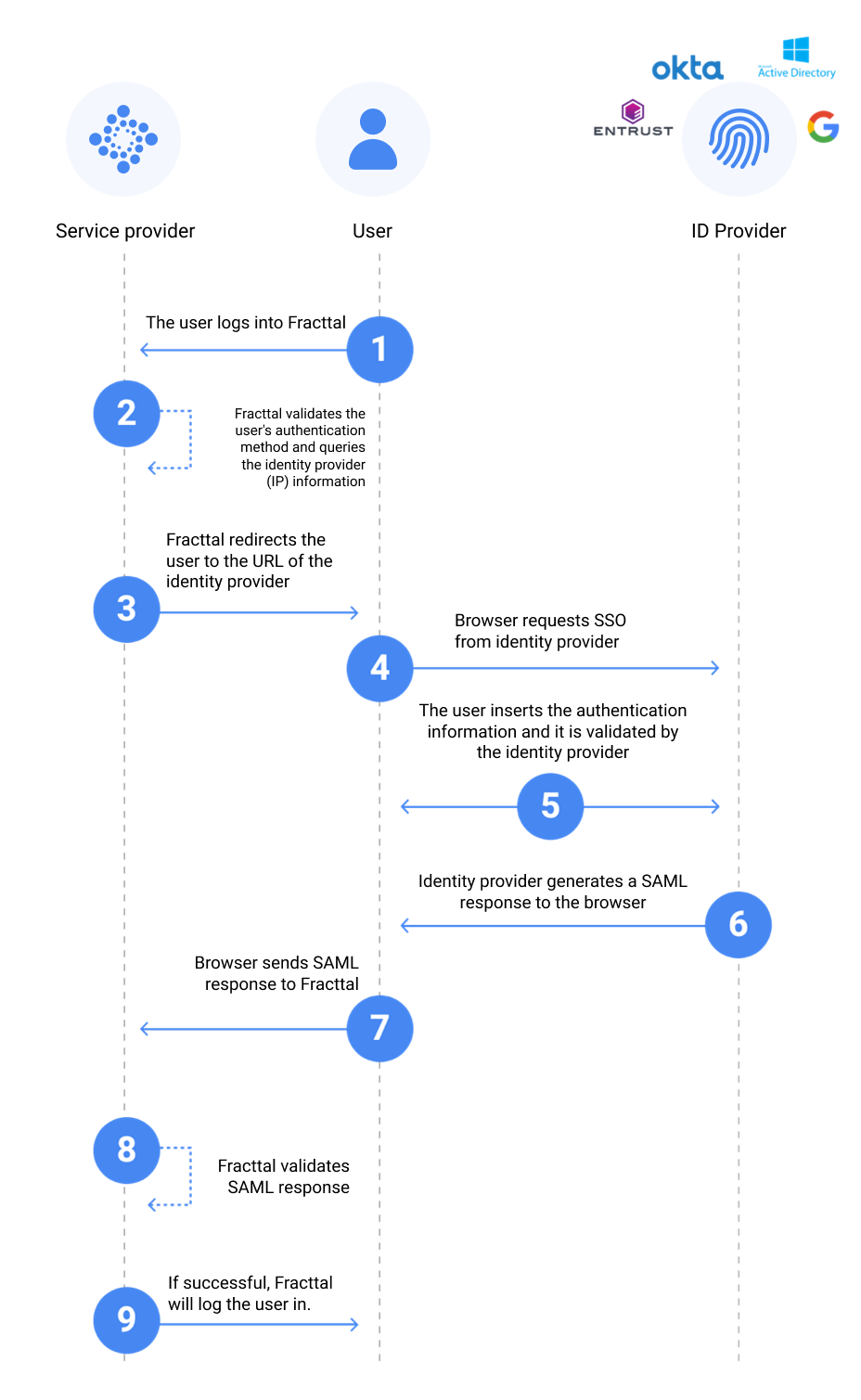
Within SSO authentication using SAML, Fracttal uses the Authentication Request Protocol, which involves receiving information related to valid or invalid login attempts.
The technical interaction of the SSO login between Fracttal and another platform can be seen in the following diagram:
Configuration for authentication with Fracttal via SAML in your identity provider
To use SAML authentication, access must be configured in the identity provider so that it recognizes the application and knows where to return the requests.
| FIELD | DESCRIPTION |
|---|---|
| EntityId | Communication Name in the identity provider. Whenever possible, use the same name used in Fracttal. |
| Attribute Consume Service Endpoint | También llamado callbackurl. URL donde se retornara la respuesta de la solicitud SAML, se debe usar la url https://one.fracttal.com/rpc/auth/samlcallback?codesaml ={codigosaml} reemplazando {codigosaml} por el campo Código SAML registrado en la configuración de Fracttal |
| Single Logout Service Endpoint | URL where the identity provider expects to receive logout requests. You should use https://one.fracttal.com. |
| NameId Format | Username format returned to Fracttal. You should use EmailAddress. |
One of the most commonly used identity providers in Fracttal is Azure Active Directory, for which you can find a configuration guide here. Click here
Updated 9 months ago
